Best in Class Cloud Monitoring and Observability
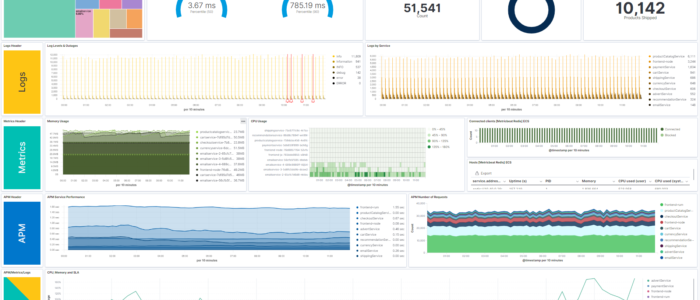
Our Machine Learning algorithms are a mix of both Art and Science. Get full visibility for your cloud infrastructure, now! Any cloud, any operating system, any time. Fully scalable and fully automated AI-based monitoring 24x7x365.



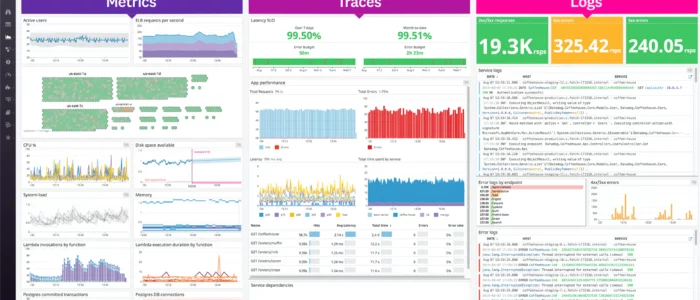
Forsee your next trouble. Get alerted before it comes!







How It Works
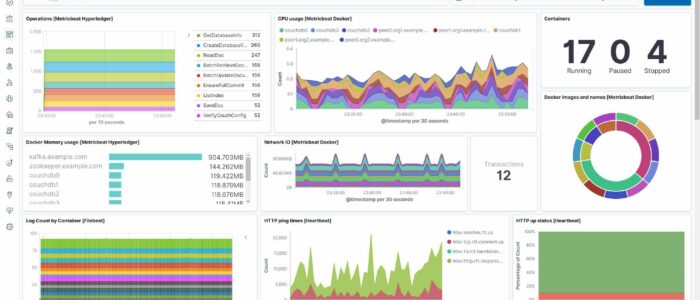
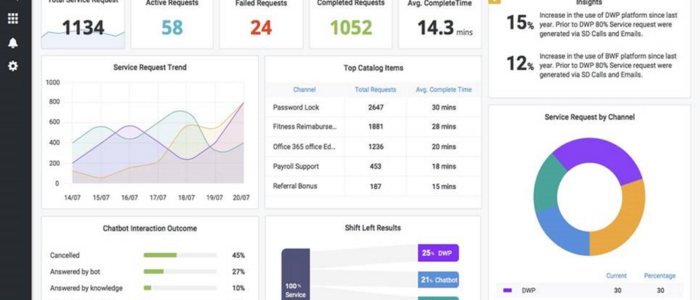
Monitor your IT infrastructure with the latest and greatest Artificial Intelligence technology! Containers and microservices, Kubernetes and service meshes, and even serverless deployments like AWS Lambda - we monitor them all. Our agents automatically collect logs and metrics from your system while delivering you real-time alerts and actionable insights on your data.